There are many tools out there that are helpful for malware development and reverse engineering. I like to use free and/or open source tools as much as possible.
You’ll find that the items in the list below are standard and very common in the industry. It’s a great idea to dedicate some time just to setting up a VM and playing around with the tools below.
Virtual Machines
VMs are very useful for malware development. They can be used for the actual development and payload generation, setting up a target or network to test against, and reverse engineering. It’s helpful to have dedicated VMs for different tasks, because they can have different operating systems, settings, software, and package management solutions.
I use VMs for 3 types of tasks related to malware development:
- Development VMs – Windows and Linux (typically an offensive distribution like Kali or Parrot).
- Target VMs – To test the malware against.
- Reverse engineering VMs – I like to use a dedicated reverse engineering VM.
VMware or VirtualBox both work well:
If you’re following along with these notes, it isn’t critical that you set all these VMs up now. I will detail exactly what VMs and software I’m using on each page.
Pre-Packaged VMs
You can download a VM and all of the above software yourself (which would be a great exercise if you aren’t already familiar with VMs), but there are also pre-packaged VM images available online.
Many of the available courses (including those from Sektor7 as well as Maldev Academy), feature pre-packaged and pre-configured VMs with these tools and more. You can get the introductory course from Sektor7 on Udemy for a very small price (under $20 at the time of this writing). The course is great and also provides a VM.
Flare VM is free and is great for setting up a reverse engineering VM.
Payload Generation
We will be using msfvenom for payload generation. Part of the Metasploit Framework, msfvenom comes pre-installed on Kali but can also be installed on Windows, OS X, and other Linux systems..
It’s extremely powerful, and it can also be used for payload encryption and other tactics used for evasion. Using msfvenom to generate payloads will be covered in-depth in a future lesson.
Development and Reverse Engineering
The following tools will be used in these notes for malware development and reverse engineering and are common in the different courses I have taken, blogs I’ve read etc.
When it comes to reverse engineering, binary analysis, etc. there are many different options available so just find the setup that works for you. Your preferences may change over time, new and better tools are always being developed, and old tools that haven’t been improved or updated in a long time fall out of favor. The most important thing is to learn the basics of the tool and try to understand what is going on.
Microsoft Visual Studio
Visual studio will be the primary IDE that I use in these notes. Note that we’re talking about ‘Visual Studio’, not ‘Visual Studio Code’.
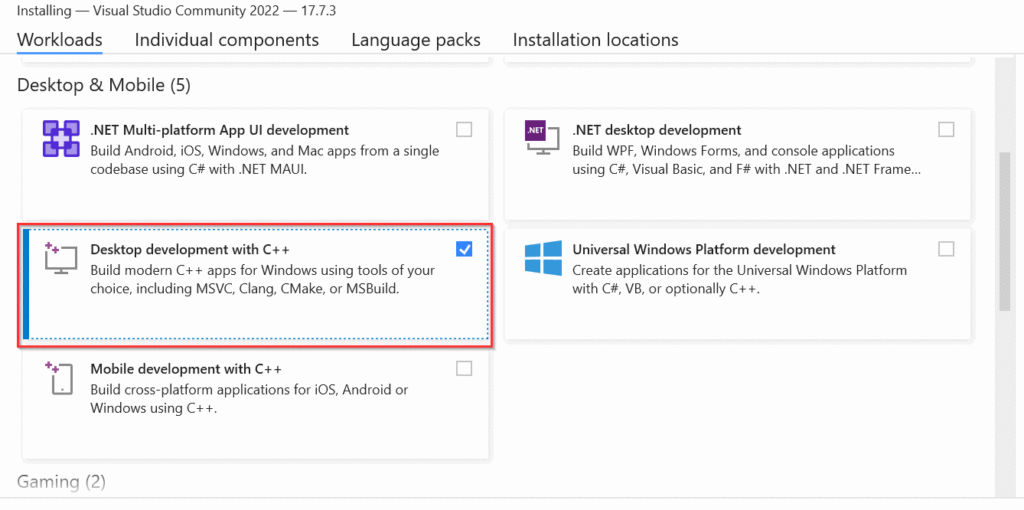
During installation, we can get support for C/C++ by selecting the ‘Desktop development with C++’ workload:
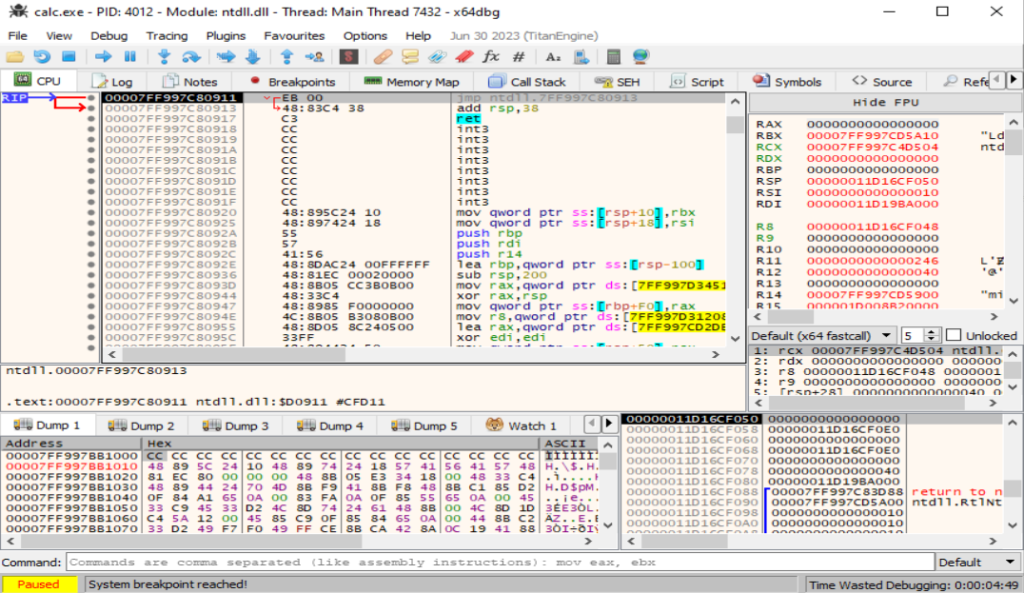
x64dbg
x64dbg is an open source debugger for Windows x86 and x64 binaries. We’ll be using this constantly.
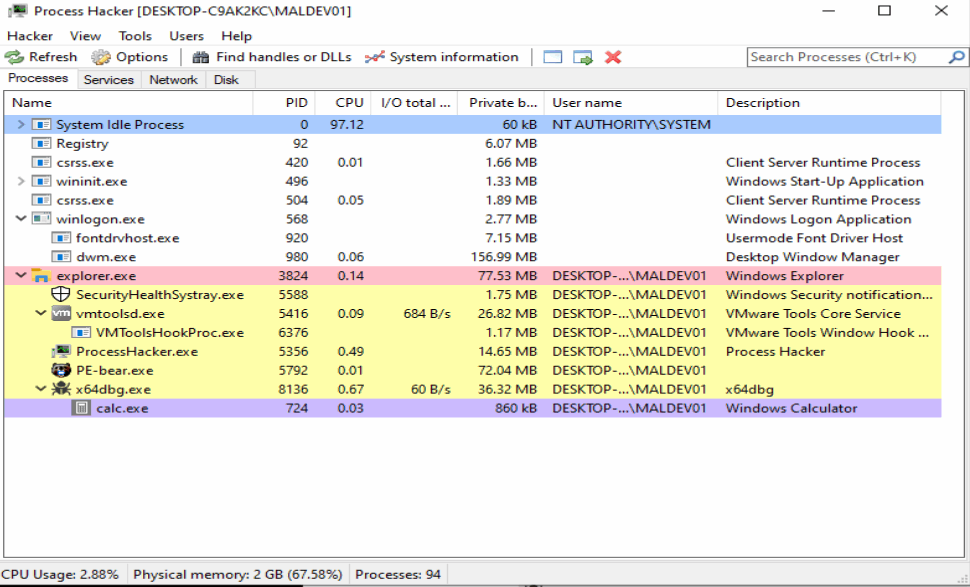
Process Hacker
Process hacker is like a super-charged version of Task Manager. It’s surprisingly handy for developing and analyzing malware.
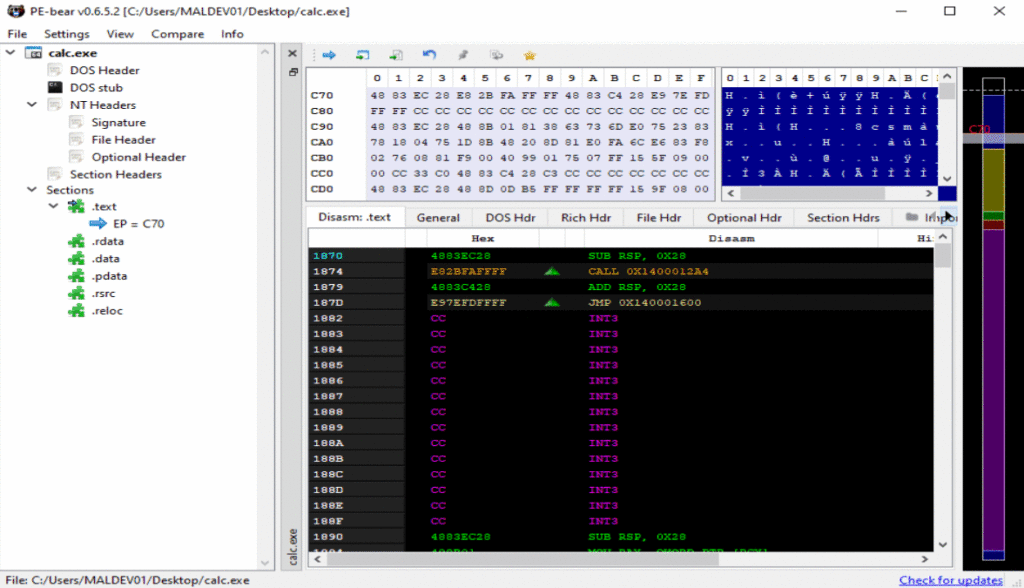
PE-Bear
PE-Bear is a powerful reverse engineering tool used by malware analysts as well as developers.