File Header
The File Header is an important structure with 7 elements that contain critical information about a portable executable. It is the second element in the NT Header, following immediately after the PE Signature.
Note that Microsoft’s documentation refers to it as the COFF File Header.
PE-Bear automatically parses the File Header for us:
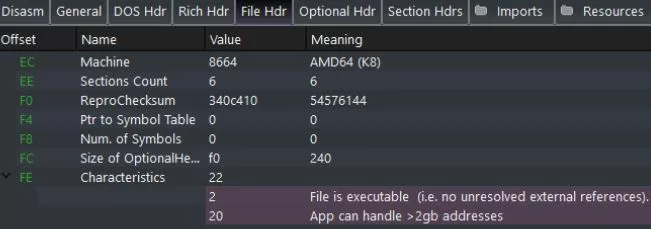
The File Header Struct
All seven (7) elements of the File Header are either type WORD (2 bytes) or DWORD (4 bytes). Here’s the entire struct:
typedef struct _IMAGE_FILE_HEADER {
WORD Machine;
WORD NumberOfSections;
DWORD TimeDateStamp;
DWORD PointerToSymbolTable;
DWORD NumberOfSymbols;
WORD SizeOfOptionalHeader;
WORD Characteristics;
} IMAGE_FILE_HEADER, *PIMAGE_FILE_HEADER;The following sections will go over each of these in detail.
Of these, the most important to make note of for malware development are NumberofSections, SizeofOptionalHeader, and Characteristics.
However reverse engineers can also use the other fields to effectively analyze, fingerprint, and extrapolate information about malware as well.
1. Machine
The machine field is a WORD (2 bytes) that specifies the target architecture of the computer. There are three possible values depending if the architecture is x86, x64, or Itanium:
| Architecture | Value |
| x86 | IMAGE_FILE_MACHINE_I386 0x014c |
| x64 | IMAGE_FILE_MACHINE_AMD64 0x8664 |
| Itanium | IMAGE_FILE_MACHINE_IA64 0x0200 |
2. NumberOfSections
The NumberofSections field is a WORD that specifies the size of the section table. The section table follows immediately after the header, and this value is limited to 96 by the Windows loader.
3. TimeDateStamp
The DWORD (4 byte) TimeDateStamp field represents the date and time that the PE file was created by the linker. It is expressed as the number of seconds since January 1, 1970 (UTC) also known as Unix timestamp.
4. PointerToSymbolTable
This DWORD holds the file offset of the symbol table and is zero if no COFF symbol table is present.
5. NumberOfSymbols
The DWORD NumberOfSymbols field indicates the number of entries in the symbol table.
6. SizeOfOptionalHeader
SizeOfOptionalHeader is an important WORD field that specifies the size of the optional header, in bytes. The optional header follows the File Header and contains additional information about the PE file, such as image base address, entry point address, and other characteristics specific to the executable.
7. Characteristics (2 bytes):
This field provides flags that indicate certain attributes of the PE file including whether it’s an executable, a DLL, a system file, and several others. The characteristics field can specify more than one characteristic, as we can see in PE-bear below:
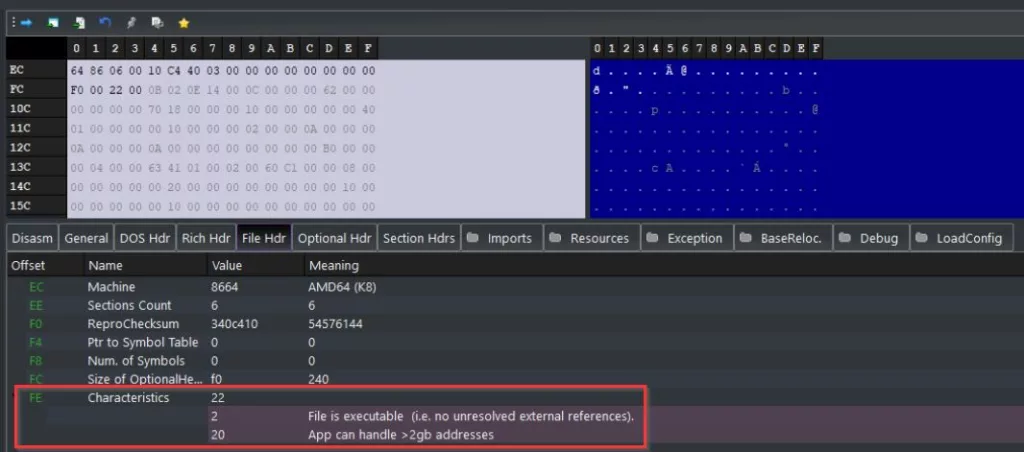
For reference, the following table shows the possible values for the characteristics flags:
| Value | Description |
|---|---|
| 0x0001 | IMAGE_FILE_RELOCS_STRIPPED – Relocation information has been stripped from the file. |
| 0x0002 | IMAGE_FILE_EXECUTABLE_IMAGE – The file is executable. |
| 0x0004 | IMAGE_FILE_LINE_NUMS_STRIPPED – The COFF line numbers were stripped from the file. |
| 0x0008 | IMAGE_FILE_LOCAL_SYMS_STRIPPED – The COFF symbol table entries were stripped from file. |
| 0x0010 | IMAGE_FILE_AGGRESIVE_WS_TRIM – (Obsolete) Trim the working set aggressively. |
| 0x0020 | IMAGE_FILE_LARGE_ADDRESS_AWARE – The app is capable of handling addresses larger than 2 GB. |
| 0x0080 | IMAGE_FILE_BYTES_REVERSED_LO – (Obsolete) The bytes of the word are reversed. |
| 0x0100 | IMAGE_FILE_32BIT_MACHINE – The machine supports 32-bit words. |
| 0x0200 | IMAGE_FILE_DEBUG_STRIPPED – Debugging information has been removed and is stored in another file. |
| 0x0400 | IMAGE_FILE_REMOVABLE_RUN_FROM_SWAP – If the image is on removable media, copy it to the swap and run it from there. |
| 0x0800 | IMAGE_FILE_NET_RUN_FROM_SWAP – If the image is on a network, copy it to the swap and run it from there. |
| 0x1000 | IMAGE_FILE_SYSTEM – The image is a system file. |
| 0x2000 | IMAGE_FILE_DLL – The image is a DLL file. |
| 0x4000 | IMAGE_FILE_UP_SYSTEM_ONLY – The file should be run only on a uniprocessor computer. |
| 0x8000 | IMAGE_FILE_BYTES_REVERSED_HI – (Obsolete) The bytes of the word are reversed. |